2.1 KiB
2.1 KiB
Questions
Part 3
- Q3.1: Setup your CI/CD pipeline with an additional SAST solution. I propose that you use
semgrepfor this task. Get your inspiration here: https://semgrep.dev/for/gitlab and https://docs.gitlab.com/ee/user/application_security/sast/ - Q3.2: Describe the found problems (alerts) in the
calculator app(in the original code, git tagv3.0) - Q3.3: Install DAST OWASP ZAP on your host or in a Docker. Play with OWASP ZAP, analyze the calculator code
- Q3.4: Implement a DAST solution in your pipeline. Get some inspiration here https://docs.gitlab.com/ee/user/application_security/dast/ . Describe what you have integrated in your pipeline. Note: you must ensure that your application is running while you are testing!
- Q3.5 (optional): Normally, the provided code has some bugs, which are discovered by SAST solution. Describe the found bugs (in the original code, git tag
v3.0) and provide solution to remediate the problems. Indicate which commit/tag contains the corrected code - Q3.6 (optional): Describe the found bugs (in the original code, git tag
v3.0) with DAST and provide solution to remediate the problems. Indicate which commit/tag contains the corrected code. Do corrections only in the provided code (no libraries)
Answers - Part 3
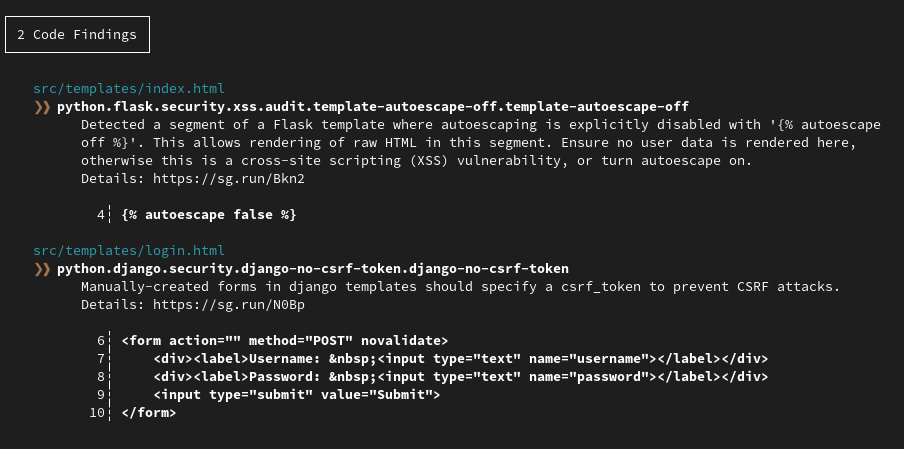
Q3.2
For some reasons, semgrep works locally, but not on GitLab. Here is the report when runned locally.
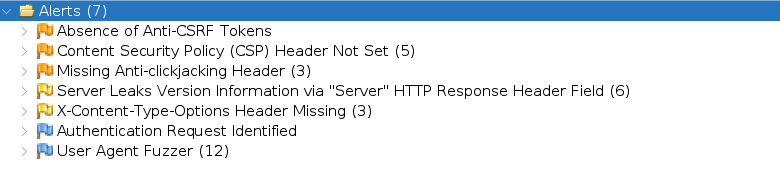
Q3.3
After performing a scan, we can see a few alerts as seen on this screenshot :
Q3.4
The integrate DAST in Github doesn't work on our version, we need the Ultimate version of GitLab selfhosted.
We create a new Docker image for the application. This image auto launch the flask app when the container is started.
We used this image as a service for the DAST stage on our CI. The stage use zaproxy to test the application. Warning do not return wailure, so the stage pass if no error is found by the OWASP ZAP.
We don't understand why the stage fail when we try to provide the html report as artifact. So if the stage fail, we can see the error in the logs.